Wireshark Packet Capture
Capturing Packets with Wireshark
8/25/20233 min read


I will be following the guided project from coursera: Wireshark for Beginners: Capture Packets by
Goal: Capture ethernet traffic and detect certain IP addressses
Scenario - Working with a company that want to detect TCP/IP traffic on their server — specifically web traffic
Set up and demonstarte Wireshark packet capture capibilties
Task 1: Adding a user a sudogroup to add packet capture capabilities
→ Key takeways: Should not run with sudo user for security reasons, SUDO is a superuser/Amdin. type of account
Task 2: Start a packet capture and save it to a file
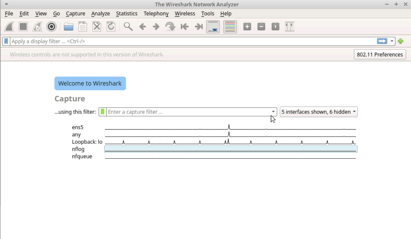
Will be selecting em5 -- as that is for ethernet traffic
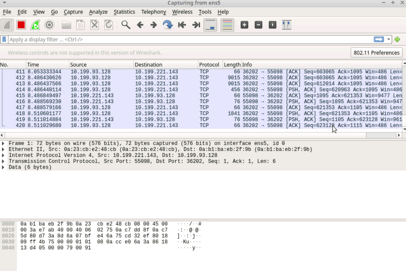
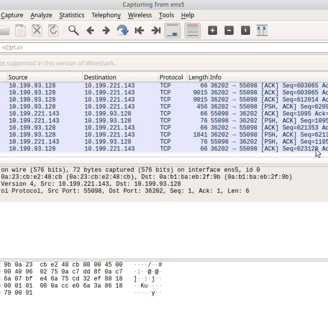
Clicking the Sharkfin logo - we can see traffic from the ethernet port
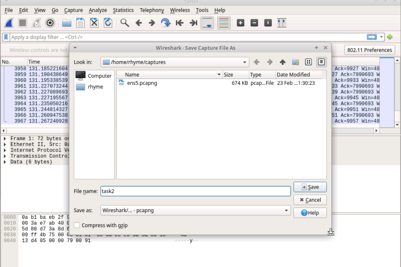
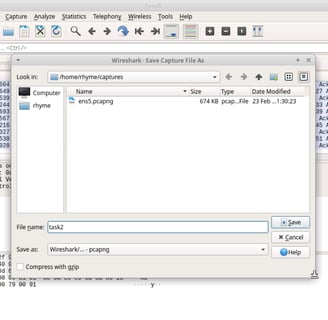
Save the packet capture in a file, Captures can only be saved when the capture is stopped.
Task 3: Use a display filter to detect HTTPS packets


We are trying to capture packets regarding the duckduckgo site. I reran wireshark and entered the url again.
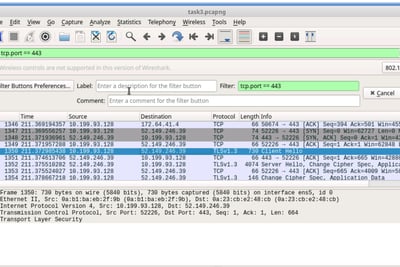
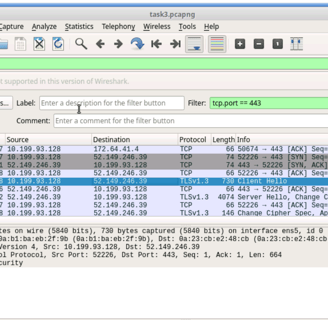
I can see the Client hello of 52.149.240.39
Entering this IP address in your browser will pull up Duckduckgo.com -- Shows that we are correctly capturing network packets
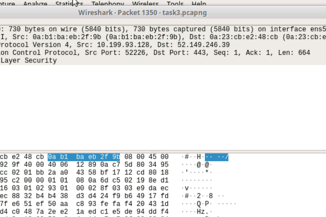
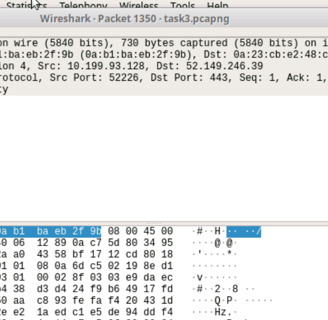
We see port 443: which is https traffic
We see that ACK -- acknowdlegemnet in the TCP handshake
We can see the packet lenght
Task 4: Visit a webpage and detect it's IP address using a display filter
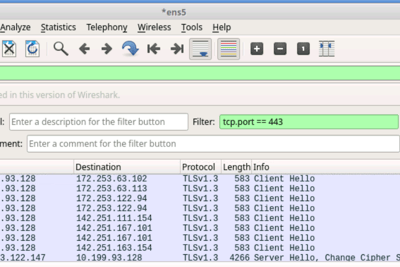
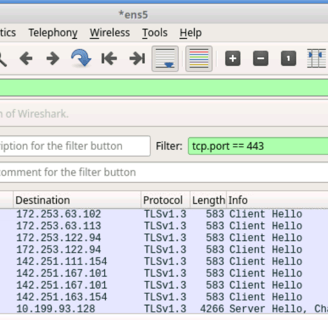
I am now capturing network traffic for: google.com
-> Here we can see multiple client hellos, this is because google uses mulitple IP addresses
We can also do this by using the filter, which will capture the first part of the TCP handshake: tls.handshake.type == 1
We can also use : ip.addr == ... to drill down into specific ip addresses (This is useful if a specific website/IP is causing issues) can use this to investigate further
ip.src == 142.251.111.154 -- When the src is communiting with our computer
ip.dst == 142.251.111.154 -- When we are sending data to this detination
Task 5: Locate all HTTPS packets from a capture not containing a certain IP address
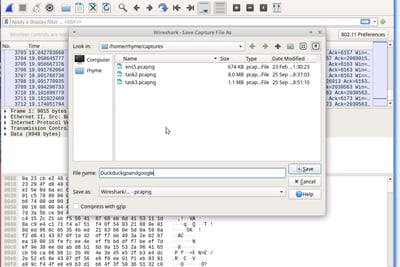
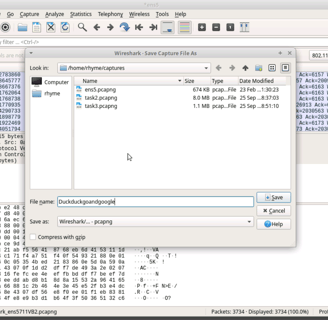
I captured data from Duckduckgo and Google and saved it to a file
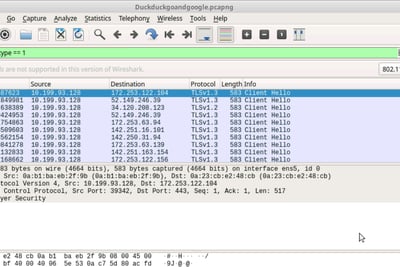
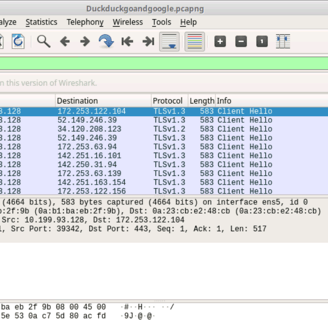
Use tls.handshake.type == 1 to look for Client hellos
The destination 172.253.122.104 is google.com
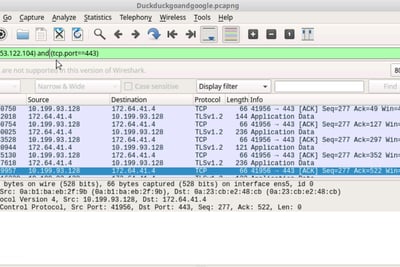
Use !ipaddr==172.253.122.104 and (tcp port==443)
This will not pick up traffic from google.com but continue to pick all other https traffic as i specified tcp port 443, can add in port 80 for HTTP traffic as well
